WTF is WAF?
Get the low-down on web application firewalls
A web application firewall (WAF) prevents unwanted traffic to and from a web application over HTTP/S. They will often be the first line of defense that protects web apps against data breaches or unauthorized code execution.
Types of WAF
- Network-based WAFs are hardware devices installed on-premises (virtual appliance options, designed to be run on public cloud platforms like AWS, Azure, or Google Cloud, are also available). They are highly performant, but can also be expensive and require a high level of maintenance.
- Host-based WAFs rely on software integrated directly into the web server . This gives them access to detailed information about the application's behavior, but may also introduce additional overhead that could affect the performance of the server.
- Cloud-based WAFs offer a balance between performance and cost-effectiveness. As a managed service, they are easy to deploy and maintain, and they provide scalability to handle traffic surges. However, they may also introduce latency due to the extra network hop.
The decision between these types of WAF will depend on several factors. These factors include the level of control and visibility you require, your budget, your team's expertise, the complexity of your network, and how much traffic you expect your application to handle.
How it Works
WAFs are often deployed through a proxy and placed in front of one or many web applications. They are capable of inspecting both inbound and outbound traffic and can identify and block many common attacks such as Cross-Site Scripting (XSS), SQL Injection, and CSRF (Cross-Site Request Forgery).
A WAF works by analyzing HTTP requests and applying a set of rules (often called a "ruleset") to identify and block potentially harmful traffic. These rulesets can be customized based on the specific needs of the application, and the firewall can also be set up to send alerts when certain types of traffic or behavior are detected.
For example, a WAF might block a request if it contains a string that matches a pattern commonly associated with SQL injection attacks (as we've covered before, WAF is useful but insufficient in this scenario).
By blocking malicious traffic and providing detailed logs of attempted attacks, a WAF can help organizations to meet their security objectives and regulatory obligations.
WAF Example
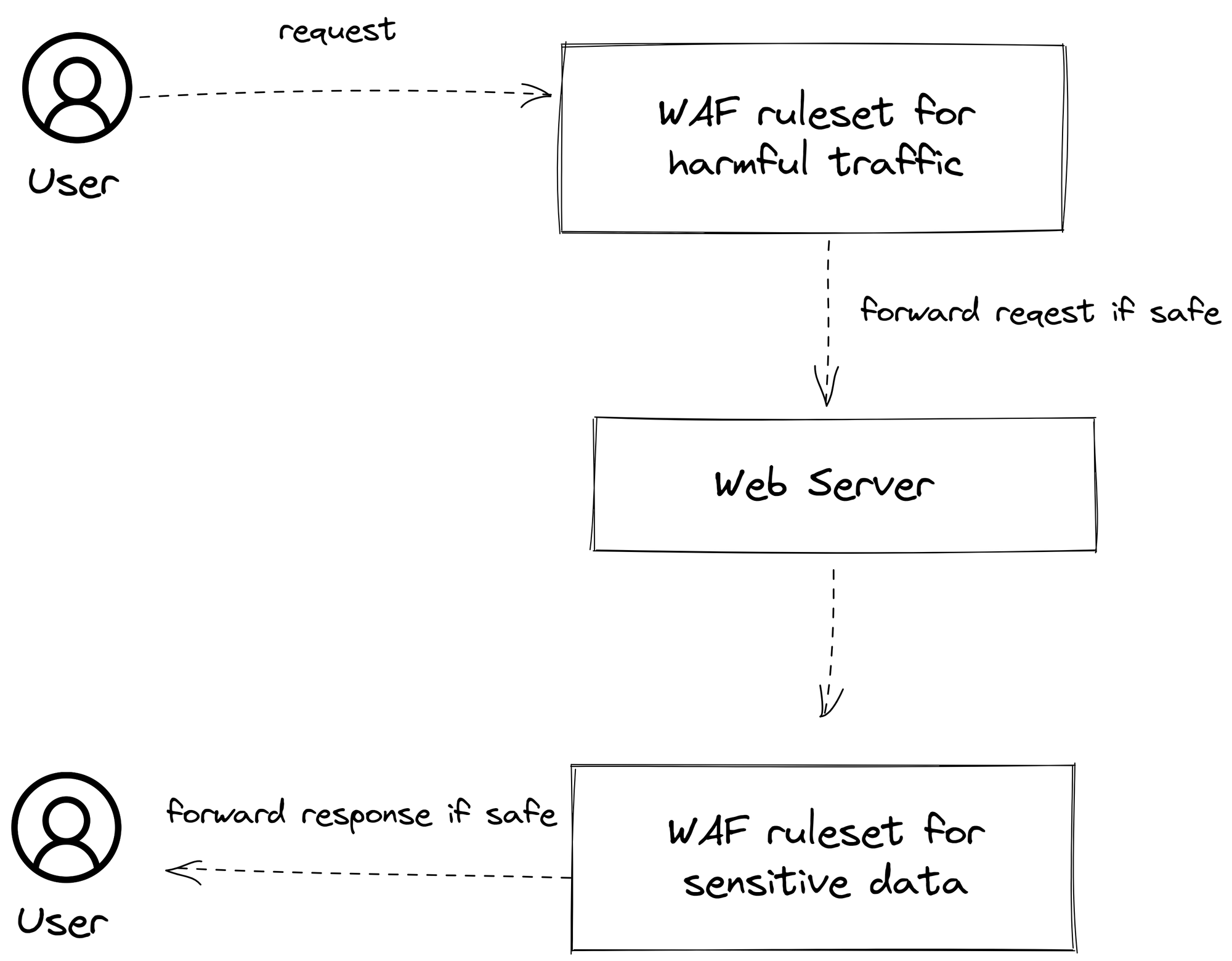
Let's break down what's happening here:
- The user makes a request to the web application. This could be anything from trying to view a webpage to submitting data through a form.
- The WAF intercepts this request before it reaches the web server. The WAF then analyzes the request based on its ruleset to determine if it's potentially harmful.
- If the request is deemed safe, it is forwarded to the web server. If the request is deemed harmful (e.g., it's identified as a common attack pattern like SQL Injection or Cross-Site Scripting), it is blocked.
- The response from the web server is then sent back to the user through the WAF, which also analyzes outbound traffic to ensure that no sensitive data is being accidentally exposed.
Commonly Used Cloud WAF Tools
| Cloud Platform | Product | Description |
|---|---|---|
| AWS | AWS WAF | AWS WAF is a web application firewall that lets you monitor the HTTP and HTTPS requests that are forwarded to Amazon CloudFront, an Amazon API Gateway API, or an Application Load Balancer. |
| Azure | Azure Web Application Firewall | Azure WAF on Azure Application Gateway provides a web application firewall (WAF) that protects your web applications from common web-based attacks like SQL injection, cross-site scripting attacks, and session hijacks. |
| GCP | Cloud Armor | Google Cloud Armor is a distributed denial of service (DDoS) defense and web application firewall (WAF) service. It provides protection for services deployed on Google Cloud. |
| Other | Cloudflare, Akamai | Cloudflare and Akamai are popular third-party WAF solutions that offer DDoS protection and traffic acceleration among other features. They can be used with any cloud provider. |